Outsmarting
Fraudsters
Designing the first "Dynamic CVV" to stop credit card theft before it happens.
Keyno
April 2019- Novemenber 2019
Product Designer
CEO and CTO
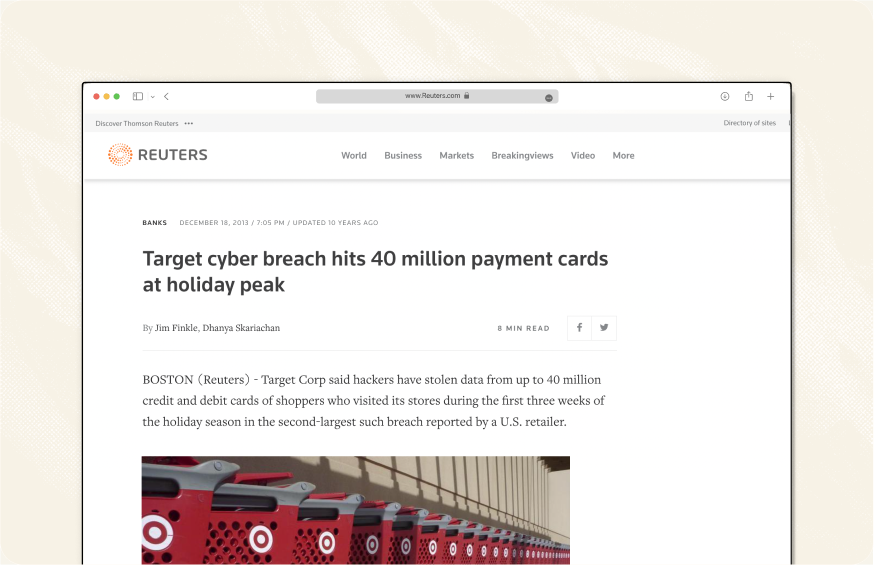
The "Target" Wake-Up Call
In 2013, hackers breached Target’s Point-of-Sale systems, stealing 40 million credit card numbers. It was a wake-up call for the industry: Static data is unsafe.The 3-digit CVV on the back of your card is a permanent password. Once a hacker has it, they can use it until the card expires.
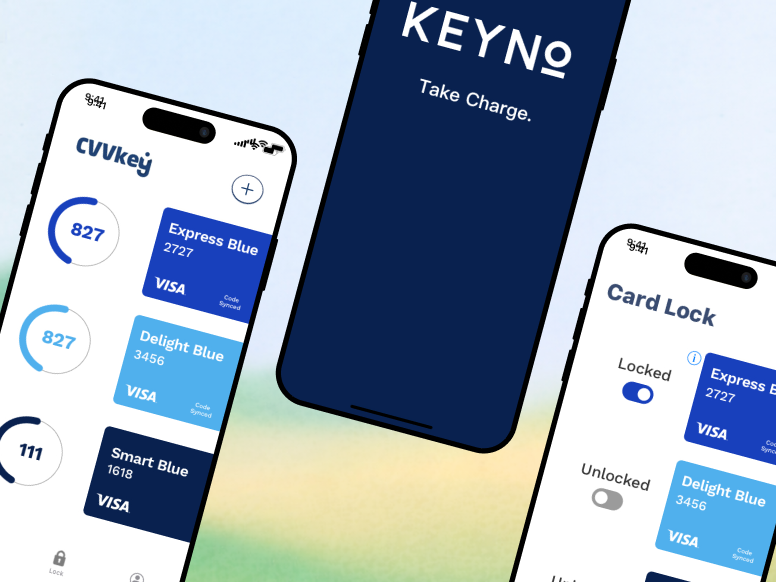
Keyno set out to build CVVKey—a technology that turns that static 3-digit code into a dynamic, rotating number (like a 2FA code) that changes every few hours. If a hacker steals your number, it’s useless by the time they try to sell it.
The "Plastic" Mental Model
The technology worked, but the user experience faced a massive psychological barrier.My research revealed that consumers view their credit card as a static, physical object. The idea that the number on the card could be different from the number in the app was confusing. It broke their mental model of how money worked.
The Friction:
Users resisted checking an app to buy something.
They didn't understand why the number changed.
Early testing showed that if the app took even 3 seconds to load, users would abandon the secure purchase and just use a different, less secure card.
The Strategy
I realized we couldn't just "educate" users; we had to visually bridge the gap between the plastic in their hand and the pixel on their screen.

The technology worked, but the user experience faced a massive psychological barrier: consumers view their credit card as a static, permanent object. The idea that a number on the card could be different from the number in the app broke their mental model of how money worked. I realized we couldn't just "educate" our way out of this; we had to design an experience that visually bridged the gap between the plastic in their wallet and the pixel on their screen.
Early Iterations
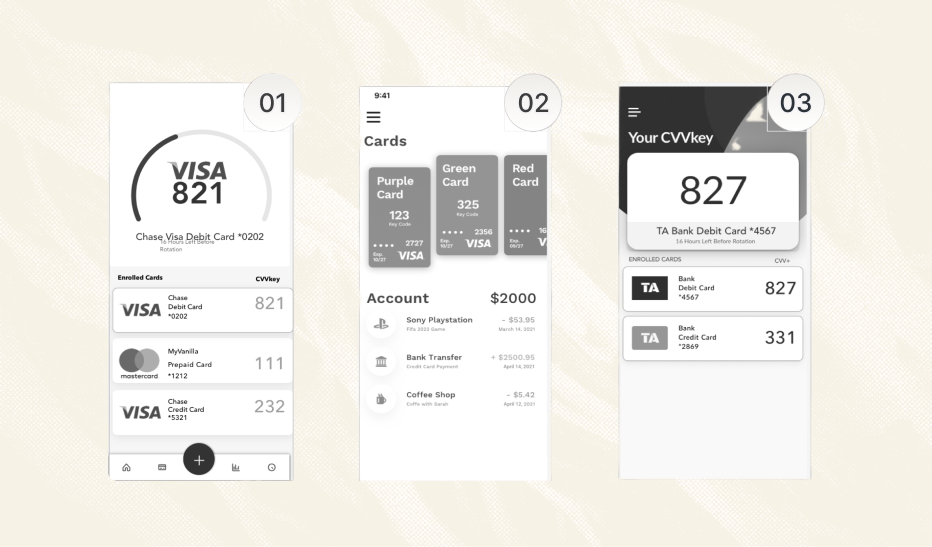
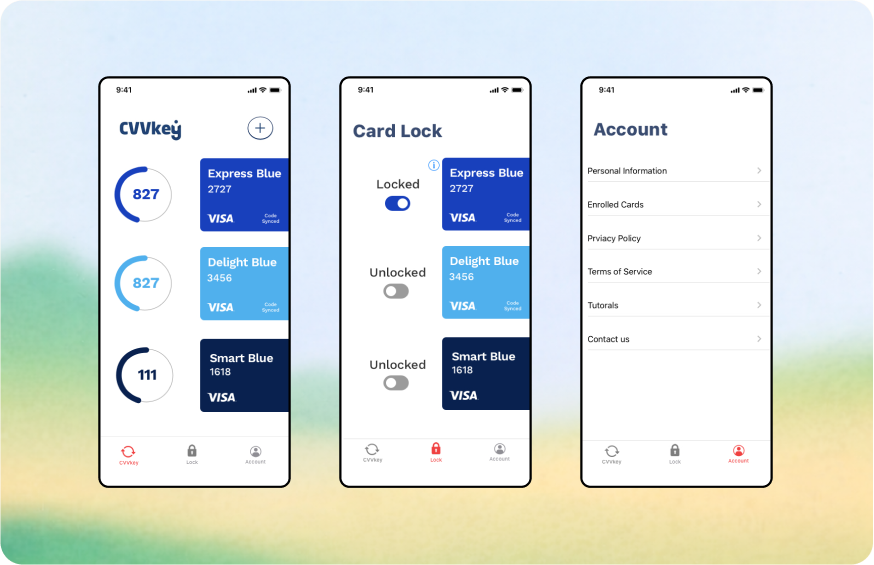
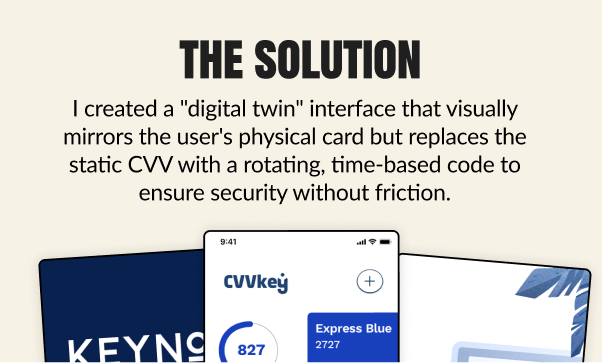
Early iterations treated the app like a generic password generator, which felt cold and disconnected from the user's finances. To fix this, I redesigned the core interface to feature a high-fidelity render of the user's specific physical card—matching the exact artwork and bank logo in their pocket.
Core Insight
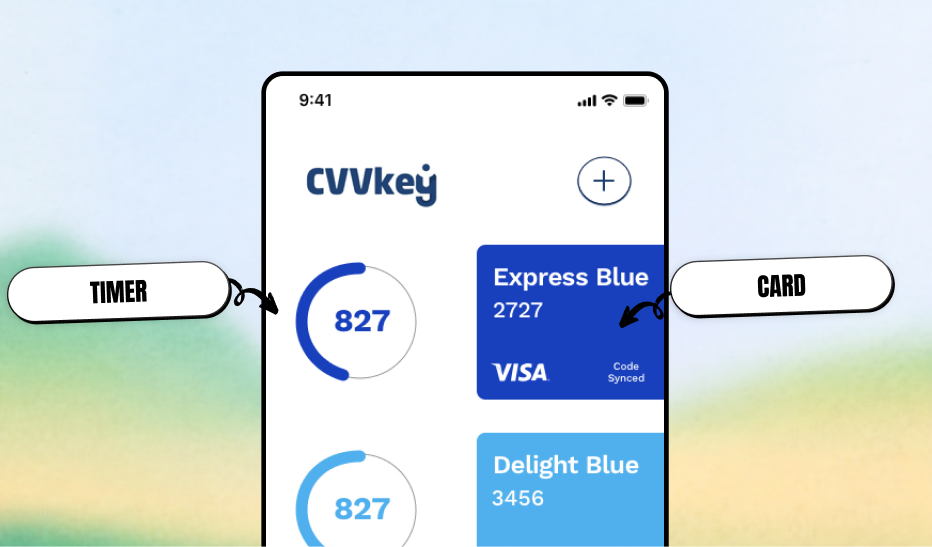
I visually "broke" the static mental model by displaying the card exactly as they knew it, except for the CVV spot, which was replaced by a glowing, digital counter. This subtle visual cue was a breakthrough: it intuitively taught users that while their card might be plastic, their security was alive and dynamic.
Final Designs
The IMpact
95%
Increase of
Application Processing
500,000
Users Across 9 Banks Worldwide
0.5%
Monthly Churn
Visa
Partnership
Industry REcgonition

The original bank-mandated enrollment flow was a seven-step ordeal requiring users to hunt for account numbers, leading to high drop-off rates. I argued that security shouldn't require a treasure hunt. We re-architected the flow to utilize authenticated sessions from the user’s existing banking app. By implementing a "silent handoff," we were able to auto-enroll users who were already logged in, cutting the flow from seven steps down to three. This shift proved that the best security experience is the one the user doesn't even notice.
Project Highlights
Next Case Study
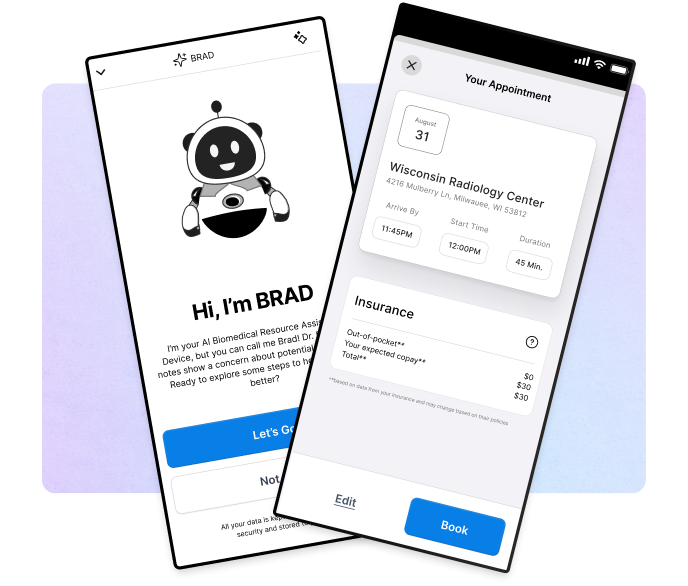
AI SIMPLIFIES
AFTER VISIT
SUMMARY
How I designed a 'Safe AI' framework to decode clinical jargon, establishing the UX patterns that now power the organization's internal intelligence engine.
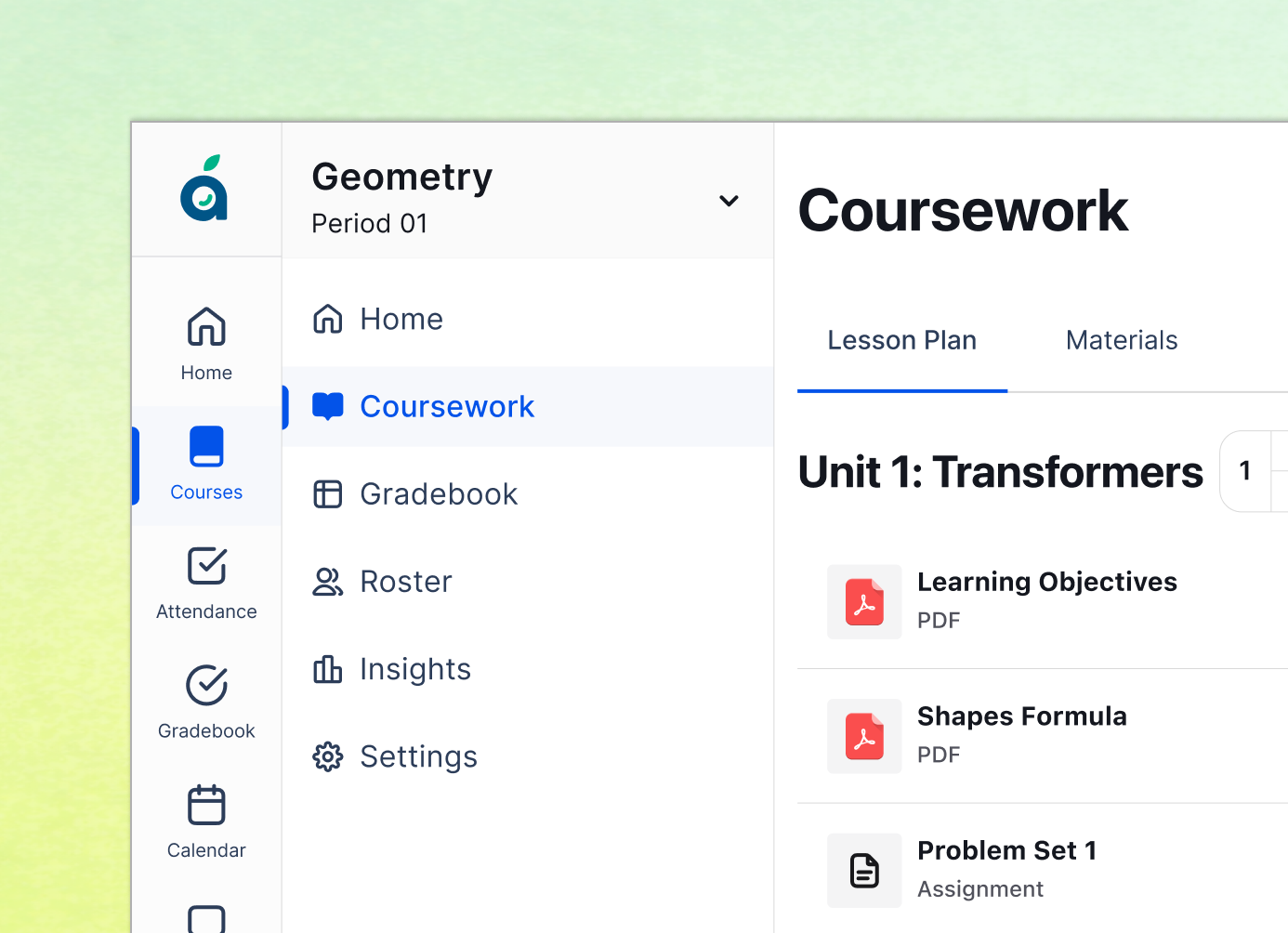
Making the Grade
Reimagining the K-12 operating system by consolidating fragmented tools into a single, schedule-aware workflow that saves teachers 45 minutes a day.
AI TAKES THE
WHEEL
Clearing a 92% backlog by designing a 'Glass Box' AI interface that increased application processing speed by 1200% in just three weeks.